Overview
The FinalCode offers the persistent way to secure sensitive document wherever they go.The Challenge
Companies face the monumental challenge of establishing strong and persistent data protection to ensure sensitive corporate information remains protected on devices, content management systems, cloud storage, and collaboration channels. Data leakage, reputation, compliance, and liability risks are amplified by many factors that fall outside an IT organisation’s oversight: Shadow IT, email, mobile devices, and much more. Plus, with robust internet connections available worldwide, it is common for many businesses to collaborate and share screens on various devices, regardless of time or place.
 |
 |
 |
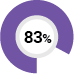
| 83% customers experienced a Document data leakage incident |
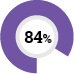
84% customers Lack confidence in Document security controls |
90% customers cannot retain persistent control over documents shared with external parties |
Our Solution
FinalCode makes implementing enterprise-grade Document encryption and granular usage control functionality easy, whether it is a SaaS or on-premise virtual appliance offering. The patented approach preserves user workflows, and Document storage and collaboration platform investments, while also protecting Documents across communication channels such as: trusted, untrusted, private or public.
Easy, Powerful, Scalable and Cost-Effective
With FinalCode, your employees can share sensitive Documents internally and externally with confidence, knowing that unauthorized recipients will not have access. This platform provides effective Document security in a host of ways:
|
Flexibility Readily works with popular applications, devices, Document storage, enterprise or cloud-based content management systems across multiple communication channels. |
Intelligence Comprehensive auditing, pattern tracking, notification, and governance across the Document usage lifecycle with the means to modify policy settings on-demand or via recipient request. |
Rapid Deployment Lightweight and efficient software client, automated onboarding, extensive directory and infrastructure interoperability, and scalable SaaS or on-premise virtual appliance. |
|
Control Granular Document permission and protection settings by owner or through enterprise policy templates: authorized users, duration, open, copy, paste, edit, save, share, print, screen capture, revoke, and remote delete. |
Security AES-256 encryption, standards-based key management, secure key server, global user access management systems, and persistent protection with application whitelisting and remote Document detection. |
How FinalCode Works
Brochures
You may download the PDF here
FinalCode®Schedule a Demo
FUJIFILM Business Innovation Internal and External File Security - FinalCode
We make it easy for you to purchase products, supplies and services from us. Our extensive network of representatives can help you choose the right solutions for your business needs.
